The evolution of car entry systems, progressing from simple mechanical keys to sophisticated remote keyless entry (RKE) and passive keyless entry (PKE) systems, has undeniably enhanced convenience for drivers. However, this technological advancement has also inadvertently opened doors for new security threats, most notably, Key Fob Hacking. As auto theft techniques become increasingly refined, understanding these vulnerabilities and the countermeasures available is crucial for vehicle security. Ultra-wideband (UWB) technology is emerging as a promising solution, offering enhanced security against common hacking methods like relay attacks, which have exploited weaknesses in Bluetooth and RFID systems.
In this article, the first of a two-part series, we will delve into the history of vehicle entry technologies and examine prevalent security breaches such as replay, rolling code, and relay attacks. We will also analyze a recent report highlighting potential vulnerabilities in Tesla’s keyless entry system, breaking down the unlocking mechanism and how it can be compromised. In the subsequent article, we will explore UWB technology in greater depth, discussing its applications and inherent security advantages in the ongoing battle against key fob hacking.
The Historical Progression and Security Lapses in Vehicle Entry Systems
The journey of vehicle entry systems began with basic mechanical keys, which, while simple, were susceptible to duplication and hot-wiring. The late 1980s marked a significant advancement with the introduction of remote keyless entry (RKE) systems. RKE allowed drivers to remotely unlock their vehicles, yet these systems soon faced their own set of security challenges. Signal jamming, interception, and replay attacks became increasingly common methods used by thieves to exploit RKE vulnerabilities.
Smart key systems, or passive keyless entry (PKE), represented the next evolution, enabling keyless entry and push-button start functionality. However, PKE systems introduced new attack vectors, particularly relay attacks. These attacks capitalize on the extended signal range of key fobs, allowing thieves to unlock and steal vehicles without direct access to the physical key. The rise in luxury car thefts due to relay attacks led to substantial increases in insurance premiums, underscoring the financial impact of key fob hacking. The escalating sophistication of these threats underscored the urgent need for more robust vehicle entry security solutions, paving the way for technologies like ultra-wideband (UWB) to enhance precision and effectively combat these advanced attack methods.
Beyond RKE and PKE, Radio Frequency Identification (RFID) technology is also integrated into many modern vehicles, often in the form of key cards or virtual keys on smartphones. RFID systems offer a degree of security due to their short-range communication, typically unlocking vehicles only within a few centimeters. However, RFID is not without its flaws. It can be susceptible to jamming by stronger signals, interception during communication, and cloning, where the RFID tag’s unique identification code is duplicated for unauthorized access.
Decoding Common Key Fob Hacking Techniques
Several signal-based attacks target vehicle entry systems, and understanding how they operate is key to appreciating the security challenges.
Jamming Attacks: In a jamming attack, hackers employ radio signals with elevated power to overwhelm and block the legitimate signals from the key fob. This effectively prevents the vehicle from receiving the correct unlock signal, resulting in a denial-of-service (DoS) scenario.
Figure 1. A jamming attack
Replay Attacks: Replay attacks involve hackers intercepting the legitimate signal transmitted from the key fob to the vehicle. By capturing and retransmitting these fixed-code signals, attackers can later gain unauthorized access to the car.
Figure 2. Diagram illustrating a replay attack on a vehicle key fob system.
Rolling Jam Attacks: A rolling jam attack is a more sophisticated method that combines signal interception and jamming techniques. Hackers simultaneously intercept the key fob signal while jamming the signal reception near the vehicle. This tactic forces the car owner to press the key fob button multiple times, unknowingly transmitting a series of rolling codes. The hackers capture these codes for potential future unauthorized access. This type of attack specifically targets vehicles equipped with rolling-code technology, which was designed to prevent replay attacks.
Figure 3. A rolling jam attack
Relay Attacks: Relay attacks exploit the signal range of key fobs to trick the vehicle into believing the key is in close proximity. Hackers use two radio devices: one placed near the vehicle and another near the victim’s key fob (even inside a house). These devices relay and amplify the key fob’s signal, effectively extending its range. This relayed signal allows the hackers to unlock and even start the vehicle as if they had the key present.
Figure 4. Diagram depicting a relay attack targeting a passive keyless entry system.
These various attack methods have proven effective against different generations of vehicle entry systems. The table below summarizes the evolution of these systems and their corresponding vulnerabilities to these hacking techniques.
| Vehicle entry system | Potential attacks |
|---|---|
| Physical key | Hot-wiring |
| Remote keyless entry (RKE) | Jamming, replay, rolling jam |
| Passive keyless entry (PKE) | Relay attack |
| RFID (key card) | Jamming, sniffing, cloning |

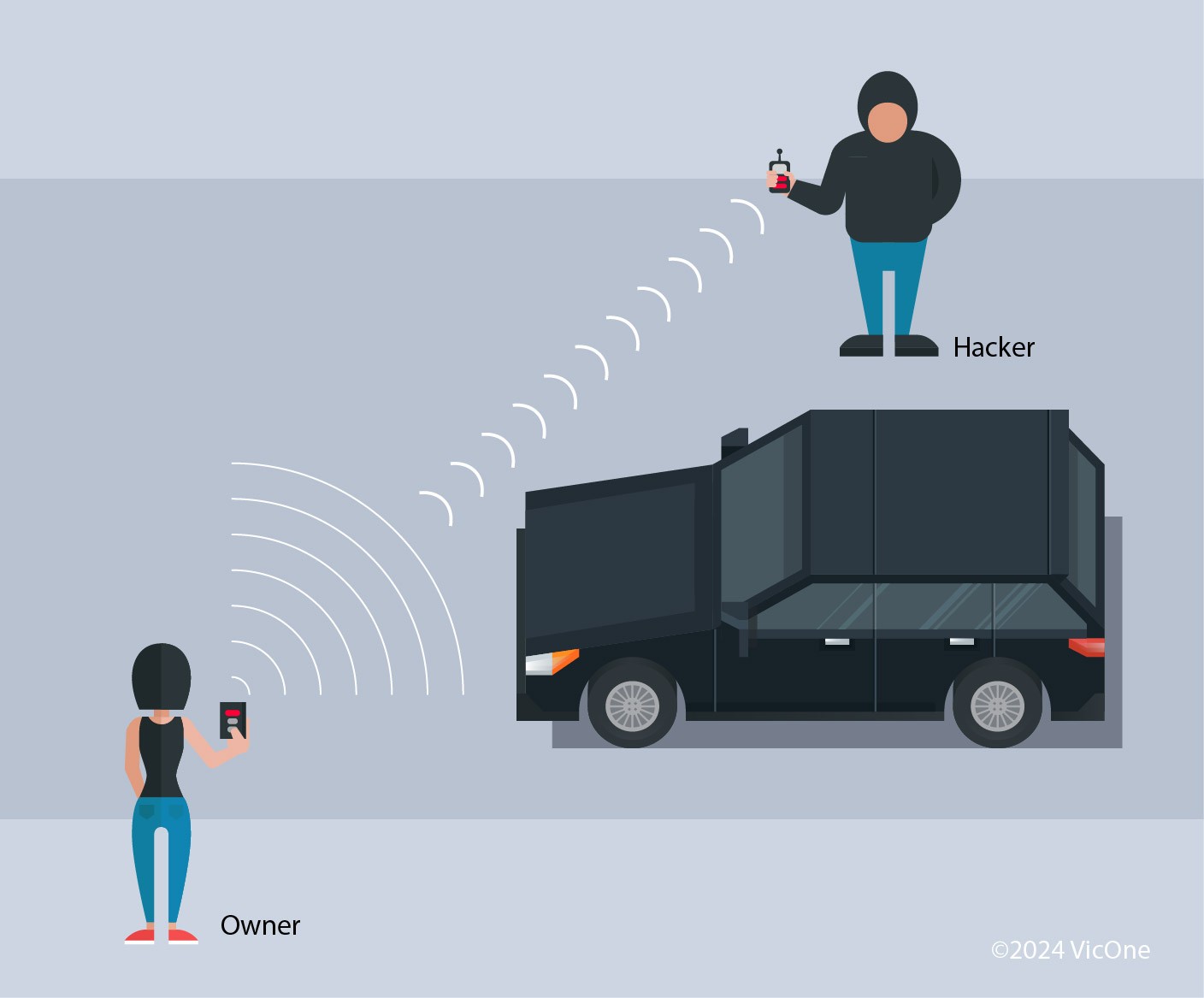
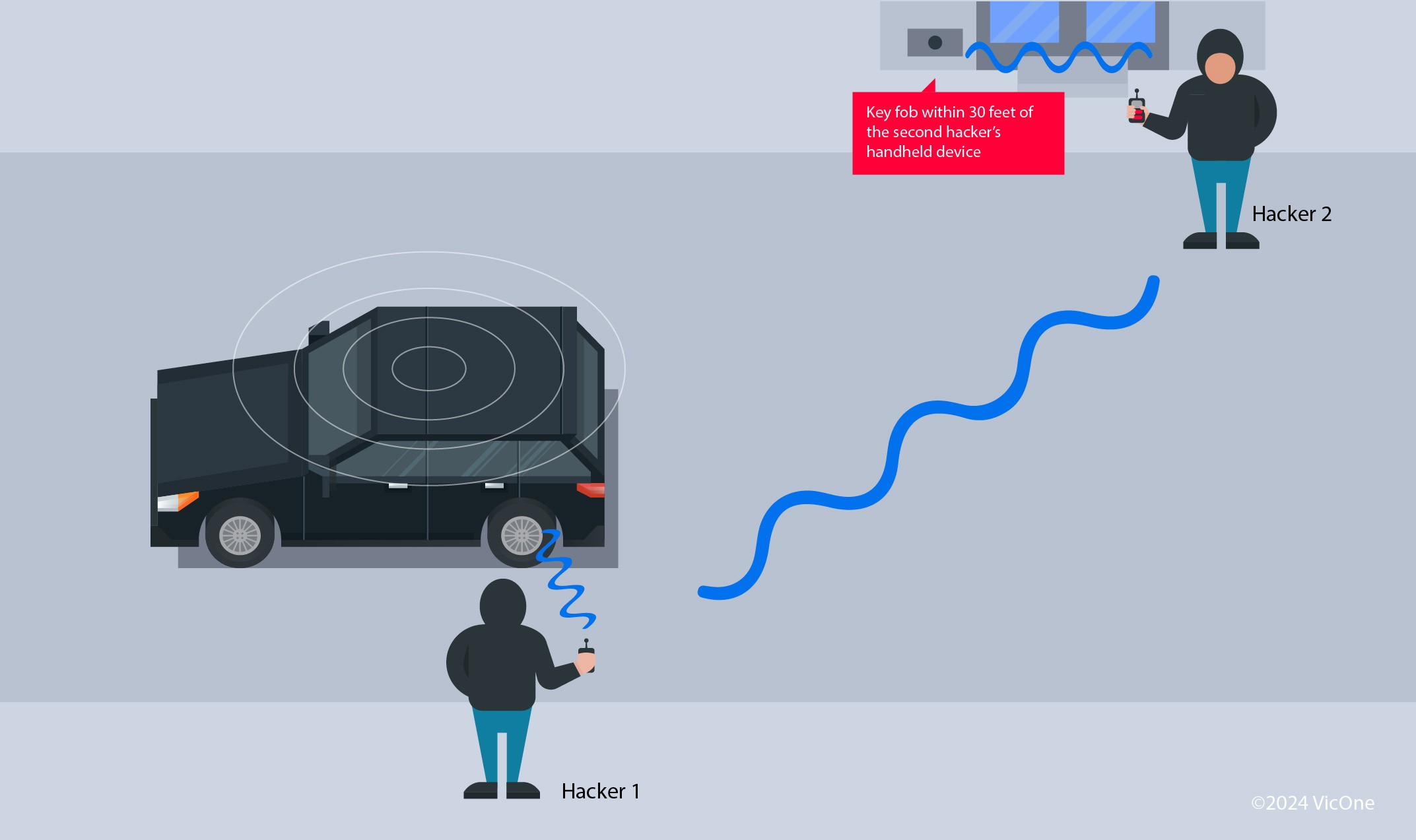
Table 1. Summary of vehicle entry systems and their vulnerabilities to different attack types.
Tesla Model 3 Vulnerability: A Case Study in Key Fob Hacking
Ultra-wideband (UWB) technology is considered a significant advancement in vehicle entry systems, promising enhanced security against radio-based attacks. However, questions remain about its effectiveness against current hacking techniques. A recent report analyzing the Tesla Model 3’s implementation of UWB sheds light on this issue.
The report, based on research by GoGoByte, indicates that despite supporting UWB, the Tesla Model 3 does not fully leverage its distance-checking capabilities to prevent relay attacks. Tesla’s keyless entry system predominantly relies on Bluetooth for unlocking and immobilizer control. Consequently, relay attacks remain successful via Bluetooth, mirroring vulnerabilities in earlier vehicle models. This highlights that simply incorporating new technology like UWB doesn’t guarantee immediate security if not properly implemented and integrated into the core security architecture.
Tesla has acknowledged these concerns and stated they are actively working to enhance the reliability and security of their UWB implementation. Until these improvements are fully deployed, Tesla vehicles remain susceptible to Bluetooth-based relay attacks. Despite this vulnerability, it’s noteworthy that Tesla vehicles are statistically reported as the least stolen vehicles in the US, largely attributed to their standard GPS tracking features. This inherent tracking capability acts as a deterrent and aids in vehicle recovery, even if theft occurs.
To further mitigate key fob hacking risks, Tesla owners are advised to utilize the “PIN-to-Drive” feature. This acts as a robust form of multi-factor authentication (MFA), requiring a four-digit PIN to be entered before the vehicle can be driven, even after successful unlocking via key fob or smartphone. PIN-to-Drive adds a crucial second layer of security, ensuring that even if a thief bypasses the keyless entry system through a relay attack, they cannot start the vehicle without the correct PIN. This feature provides a practical and effective safeguard against current security weaknesses until more comprehensive UWB security measures are in place.
The Tesla Model 3 case study underscores the ongoing need for continuous improvement and robust implementation of advanced security technologies like UWB to truly counter evolving key fob hacking techniques. In the second part of this blog series, we will delve deeper into UWB technology, exploring its potential to revolutionize vehicle security and effectively combat sophisticated attacks.
